quinta-feira, 29 de junho de 2023
Quem te guia é Jesus
Quando Nabucodonosor mandou levantar uma grande estátua. e quando o povo estava pronto para sujeitar-se aos caprichos do rei e adorar a estátua que fora levantada; eis que:
"Ora, no mesmo instante, se chegaram alguns homens caldeus e acusaram os judeus;" (Dn 3:8)
Porque exatamente uns poucos não estavam se sujeitando ao fato, como foi o caso de Hananias, Misael e Azarias, que passaram a se chamar Sadraque, Mesaque e Abede-Nego.
"Há uns homens judeus, que tu constituíste sobre os negócios da província da Babilônia: Sadraque, Mesaque e Abede-Nego; estes homens, ó rei, não fizeram caso de ti, a teus deuses não servem, nem adoram a imagem de ouro que levantaste." (Dn 3:12)
"Responderam Sadraque, Mesaque e Abede-Nego ao rei: Ó Nabucodonosor, quanto a isto não necessitamos de te responder.
Se o nosso Deus, a quem servimos, quer livrar-nos, ele nos livrará da fornalha de fogo ardente e das tuas mãos, ó rei.
Se não, fica sabendo, ó rei, que não serviremos a teus deuses, nem adoraremos a imagem de ouro que levantaste." (Dn 3:16-18)
"Então, se chegou Nabucodonosor à porta da fornalha sobremaneira acesa, falou e disse: Sadraque, Mesaque e Abede-Nego, servos do Deus Altíssimo, saí e vinde! Então, Sadraque, Mesaque e Abede-Nego saíram do meio do fogo." (Dn 3:26)
"Falou Nabucodonosor e disse: Bendito seja o Deus de Sadraque, Mesaque e Abede-Nego, que enviou o seu anjo e livrou os seus servos, que confiaram nele, pois não quiseram cumprir a palavra do rei, preferindo entregar o seu corpo, a servirem e adorarem a qualquer outro deus, senão ao seu Deus.
Portanto, faço um decreto pelo qual todo povo, nação e língua que disser blasfêmia contra o Deus de Sadraque, Mesaque e Abede-Nego seja despedaçado, e as suas casas sejam feitas em monturo; porque não há outro deus que possa livrar como este.
Então, o rei fez prosperar a Sadraque, Mesaque e Abede-Nego na província da Babilônia." (Dn 3:28-30)
(ap. Ely Silmar Vidal - Teólogo: COJAE 0001-12-PF-BR; Psicanalista: CONIPSI CIP: 0001-12-PF-BR; Jornalista: DRT-9597/PR e presidente do CIEP - Clube de Imprensa Estado do Paraná)
Contato:
(41) 98514-8333
(41) 99109-8374
(41) 99821-2381 e 99820-9599 (WhatsApp)
Mensagem 04032023 - Quem te guia é Jesus - (imagens da internet)
Os trabalhos que desenvolvo, não visam lucros financeiros, e são, apenas divulgação do que acho interessante para conhecimento geral, por isso, não monetizo.
Que o Espírito Santo do Senhor nos oriente a todos para que possamos iluminar um pouquinho mais o caminho de nossos irmãos, por isso contamos contigo.
Se a mensagem foi útil, e acha que pode ajudar alguém, divulgue: (ao replicar, preserve a fonte)
Siga-nos: https://www.bitchute.com/video/hF2y21d2I9e4/
Texto completo e outros em: http://www.portaldaradio.com
[category economia,politica,ffaa,cristianismo,pensamentos,psicanalise,historia,noticias]
@elyvidal @radiocrista @pastorelyvidal @conipsip @CiepClube
#FalaPortaldaRadio #conipsi #cojae #dojae
quinta-feira, 22 de junho de 2023
Louvar a Deus
Foi para isso que você veio ao mundo, louvar a Deus, quando anda, quando come, quando descansa, enfim, louvar a Deus em todo tempo e com todas as tuas forças.
O demais, como seja, viver bem, por exemplo, isso acontecerá, quanto mais a sua dedicação for em louvar ao Senhor.
Quando todas as nossas forças estão voltadas para A ou para B, naturalmente que a força escolhida, será mais ou menos expressiva em tua vida. Quando o jovem sai em busca de bebidas, drogas, etc... Nota-se então, que esses pontos eleitos como fatores de sua atenção, o levarão à satisfação do que seu corpo exige, e por conseguinte, a resposta será a do afastamento de Deus. E se a resposta for do afastamento, naturalmente, que isso acontecerá com as consequências naturais pela escolha feita.
Então louvar a Deus é a tônica para a nossa vida, no entanto, o que mais percebemos é que a vida nos indica caminhos que não são muito adequados. Isso, desagrada a Deus, porque Ele exige todo louvor, toda a honra e toda a Glória que lhe é devida, e ainda complementa com o fato de que, Ele não divide a Sua glória com ninguém.
"Tributai ao Senhor, ó famílias dos povos, tributai ao Senhor glória e força.
Tributai ao Senhor a glória devida ao seu nome; trazei oferendas e entrai nos seus átrios.
Adorai o Senhor na beleza da sua santidade; tremei diante dele, todas as terras.
Dizei entre as nações: Reina o Senhor. Ele firmou o mundo para que não se abale e julga os povos com equidade.
Alegrem-se os céus, e a terra exulte; ruja o mar e a sua plenitude.
Folgue o campo e tudo o que nele há; regozijem-se todas as árvores do bosque, na presença do Senhor, porque vem, vem julgar a terra; julgará o mundo com justiça e os povos, consoante a sua fidelidade." (Sl 96:7-13)
Primeiramente, que cada um tome a sua cruz, e siga em direção a tudo o que determina a Santa e Sagrada Palavra, para que tenha uma vida, que sendo santa, será agradável a Deus e portanto, te será abençoadara, para que tenhas vida longa e saudável.
Não esqueça de exortar ao próximo nos caminhos em que deve andar, porque sim, tu és guardador de teus irmãos sobre a face da terra; e procedendo assim, estará pagando teus votos, pela vida que Ele tão generosamente te tem proporcionado.
(ap. Ely Silmar Vidal - Teólogo: COJAE 0001-12-PF-BR; Psicanalista: CONIPSI CIP: 0001-12-PF-BR; Jornalista: DRT-9597/PR e presidente do CIEP - Clube de Imprensa Estado do Paraná)
Contato:
(41) 98514-8333
(41) 99109-8374
(41) 99821-2381 e 99820-9599 (WhatsApp)
Mensagem 03032023 - Louvar a Deus - (imagens da internet)
Os trabalhos que desenvolvo, não visam lucros financeiros, e são, apenas divulgação do que acho interessante para conhecimento geral, por isso, não monetizo.
Que o Espírito Santo do Senhor nos oriente a todos para que possamos iluminar um pouquinho mais o caminho de nossos irmãos, por isso contamos contigo.
Se a mensagem foi útil, e acha que pode ajudar alguém, divulgue: (ao replicar, preserve a fonte)
Siga-nos: https://www.bitchute.com/video/DRj0kiZMi1J5/
Texto completo e outros em: http://www.portaldaradio.com
[category economia,politica,ffaa,cristianismo,pensamentos,psicanalise,historia,noticias]
@elyvidal @radiocrista @pastorelyvidal @conipsip @CiepClube
#FalaPortaldaRadio #conipsi #cojae #dojae
quarta-feira, 14 de junho de 2023
A revelação da glória de Deus na Palavra
O objetivo a cada leitura, cada vírgula, cada novo termo é apenas ilustrar e revelar cada vez mais a face do Senhor.
Como havia pedido Moisés:
"Então, ele disse: Rogo-te que me mostres a tua glória.
Respondeu-lhe: Farei passar toda a minha bondade diante de ti e te proclamarei o nome do Senhor; terei misericórdia de quem eu tiver misericórdia e me compadecerei de quem eu me compadecer.
E acrescentou: Não me poderás ver a face, porquanto homem nenhum verá a minha face e viverá.
Disse mais o Senhor: Eis aqui um lugar junto a mim; e tu estarás sobre a penha.
Quando passar a minha glória, eu te porei numa fenda da penha e com a mão te cobrirei, até que eu tenha passado.
Depois, em tirando eu a mão, tu me verás pelas costas; mas a minha face não se verá." (Êx 33:18-23)
por essa passagem vemos, embora de forma indelével, mas muito objetiva, a descrição da glória do Senhor.
Ou seja, Ele nos diz, que tudo o que devemos saber acerca dEle, de Sua graça e misericórdia, já está revelada ao longo da meditação da Palavra e da observância do que seja a dinamicidade da vida.
Nada foi ocultado, apenas e tão somente, muitos de nós não veremos muita coisa, por conta da incredulidade que nos domina e por consequência do afastamento a que nos submetemos, até a ponto da apostasia.
Devemos sempre ter em mente o arrependimento e uma oração pela clemência de Deus sobre nossas vidas, como o pedido de perdão de Simei a Davi:
"Não me imputes, senhor, a minha culpa e não te lembres do que tão perversamente fez teu servo, no dia em que o rei, meu senhor, saiu de Jerusalém; não o conserves, ó rei, em teu coração." (2 Sm 19:19)
E Deus te responderá ao notar em teu coração a verdade em tuas palavras:
"Não morrerás. E lho jurou." (2 Sm 19:23)
(ap. Ely Silmar Vidal - Teólogo: COJAE 0001-12-PF-BR; Psicanalista: CONIPSI CIP: 0001-12-PF-BR; Jornalista: DRT-9597/PR e presidente do CIEP - Clube de Imprensa Estado do Paraná)
Contato:
(41) 98514-8333
(41) 99109-8374
(41) 99821-2381 e 99820-9599 (WhatsApp)
Mensagem 19042023 - A revelação da glória de Deus na Palavra - (imagens da internet)
Os trabalhos que desenvolvo, não visam lucros financeiros, e são, apenas divulgação do que acho interessante para conhecimento geral, por isso, não monetizo.
Que o Espírito Santo do Senhor nos oriente a todos para que possamos iluminar um pouquinho mais o caminho de nossos irmãos, por isso contamos contigo.
Se a mensagem foi útil, e acha que pode ajudar alguém, divulgue: (ao replicar, preserve a fonte)
Siga-nos: https://www.bitchute.com/video/kvzTgzXz57RX
Texto completo e outros em: http://www.portaldaradio.com
[category economia,politica,ffaa,cristianismo,pensamentos,psicanalise,historia,noticias]
@elyvidal @radiocrista @pastorelyvidal @conipsip @CiepClube
#FalaPortaldaRadio #conipsi #cojae #dojae
domingo, 11 de junho de 2023
Abra o teu coração
"Uma vez em terra, verificamos que a ilha se chamava Malta.
Os bárbaros trataram-nos com singular humanidade, porque, acendendo uma fogueira, acolheram-nos a todos por causa da chuva que caía e por causa do frio.
Tendo Paulo ajuntado e atirado à fogueira um feixe de gravetos, uma víbora, fugindo do calor, prendeu-se-lhe à mão.
Quando os bárbaros viram a víbora pendente da mão dele, disseram uns aos outros: Certamente, este homem é assassino, porque, salvo do mar, a Justiça não o deixa viver.
Porém ele, sacudindo o réptil no fogo, não sofreu mal nenhum; mas eles esperavam que ele viesse a inchar ou a cair morto de repente. Mas, depois de muito esperar, vendo que nenhum mal lhe sucedia, mudando de parecer, diziam ser ele um deus.
Perto daquele lugar, havia um sítio pertencente ao homem principal da ilha, chamado Públio, o qual nos recebeu e hospedou benignamente por três dias.
Aconteceu achar-se enfermo de disenteria, ardendo em febre, o pai de Públio. Paulo foi visitá-lo, e, orando, impôs-lhe as mãos, e o curou.
À vista deste acontecimento, os demais enfermos da ilha vieram e foram curados, os quais nos distinguiram com muitas honrarias; e, tendo nós de prosseguir viagem, nos puseram a bordo tudo o que era necessário.
Ao cabo de três meses, embarcamos num navio alexandrino, que invernara na ilha e tinha por emblema Dióscuros.
Tocando em Siracusa, ficamos ali três dias, donde, bordejando, chegamos a Régio. No dia seguinte, tendo soprado vento sul, em dois dias, chegamos a Putéoli, onde achamos alguns irmãos que nos rogaram ficássemos com eles sete dias; e foi assim que nos dirigimos a Roma.
Tendo ali os irmãos ouvido notícias nossas, vieram ao nosso encontro até à Praça de Ápio e às Três Vendas. Vendo-os Paulo e dando, por isso, graças a Deus, sentiu-se mais animado.
Uma vez em Roma, foi permitido a Paulo morar por sua conta, tendo em sua companhia o soldado que o guardava.
Três dias depois, ele convocou os principais dos judeus e, quando se reuniram, lhes disse: Varões irmãos, nada havendo feito contra o povo ou contra os costumes paternos, contudo, vim preso desde Jerusalém, entregue nas mãos dos romanos; os quais, havendo-me interrogado, quiseram soltar-me sob a preliminar de não haver em mim nenhum crime passível de morte.
Diante da oposição dos judeus, senti-me compelido a apelar para César, não tendo eu, porém, nada de que acusar minha nação.
Foi por isto que vos chamei para vos ver e falar; porque é pela esperança de Israel que estou preso com esta cadeia.
Então, eles lhe disseram: Nós não recebemos da Judeia nenhuma carta que te dissesse respeito; também não veio qualquer dos irmãos que nos anunciasse ou dissesse de ti mal algum.
Contudo, gostaríamos de ouvir o que pensas; porque, na verdade, é corrente a respeito desta seita que, por toda parte, é ela impugnada.
Havendo-lhe eles marcado um dia, vieram em grande número ao encontro de Paulo na sua própria residência. Então, desde a manhã até à tarde, lhes fez uma exposição em testemunho do reino de Deus, procurando persuadi-los a respeito de Jesus, tanto pela lei de Moisés como pelos profetas.
Houve alguns que ficaram persuadidos pelo que ele dizia; outros, porém, continuaram incrédulos.
E, havendo discordância entre eles, despediram-se, dizendo Paulo estas palavras: Bem falou o Espírito Santo a vossos pais, por intermédio do profeta Isaías, quando disse: Vai a este povo e dize-lhe: De ouvido, ouvireis e não entendereis; vendo, vereis e não percebereis.
Porquanto o coração deste povo se tornou endurecido; com os ouvidos ouviram tardiamente e fecharam os olhos, para que jamais vejam com os olhos, nem ouçam com os ouvidos, para que não entendam com o coração, e se convertam, e por mim sejam curados.
Tomai, pois, conhecimento de que esta salvação de Deus foi enviada aos gentios. E eles a ouvirão.
[Ditas estas palavras, partiram os judeus, tendo entre si grande contenda.]
Por dois anos, permaneceu Paulo na sua própria casa, que alugara, onde recebia todos que o procuravam, pregando o reino de Deus, e, com toda a intrepidez, sem impedimento algum, ensinava as coisas referentes ao Senhor Jesus Cristo." (At 28:1-31)
(ap. Ely Silmar Vidal - Teólogo: COJAE 0001-12-PF-BR; Psicanalista: CONIPSI CIP: 0001-12-PF-BR; Jornalista: DRT-9597/PR e presidente do CIEP - Clube de Imprensa Estado do Paraná)
Contato:
(41) 98514-8333
(41) 99109-8374
(41) 99821-2381 e 99820-9599 (WhatsApp)
Mensagem 02032023 - Abra o teu coração - (imagens da internet)
Os trabalhos que desenvolvo, não visam lucros financeiros, e são, apenas divulgação do que acho interessante para conhecimento geral, por isso, não monetizo.
Que o Espírito Santo do Senhor nos oriente a todos para que possamos iluminar um pouquinho mais o caminho de nossos irmãos, por isso contamos contigo.
Se a mensagem foi útil, e acha que pode ajudar alguém, divulgue: (ao replicar, preserve a fonte)
Siga-nos: https://www.bitchute.com/video/vpIzxncdM5Za/
Texto completo e outros em: http://www.portaldaradio.com
[category economia,politica,ffaa,cristianismo,pensamentos,psicanalise,historia,noticias]
@elyvidal @radiocrista @pastorelyvidal @conipsip @CiepClube
#FalaPortaldaRadio #conipsi #cojae #dojae
sábado, 10 de junho de 2023
will Do Verify the factory,Sample Collection, Negotiation, Dropshipping, Shipping, After-Sales Follow-up, Search, Etc.
hello
Hope this finds you well.
I can be your sourcing agent in China.
Tired of a middle-men charging your higher prices?
Lower effectively communication with factory or salesman?
Delay the factory delivery time one time and one time?
Manufacture can't accept your Mini order?
Why I am a professional China sourcing agent?
Procurement process:
1.MARKET INFORMATION COLLECTION
1>Sourcing consult 2>Trading suggestions 3>Shipping suggestions 4>Industrial analysis
2.SOURCING REPORT WITH SUGGESTIONS
1>Sourcing report 2> Production time and shipping cost estimate 3>Product upgrade(Open mold)
3.SOURCING SAMPLE PRODUCTION SHIPPING
1>Sample collection and review 2>Negotiation 3>Production arrange. 4>Shipping arrange.
Much appreciated if you could assign this to the responsible party.
We are dedicated to help small & medium overseas companies or individual sourcing from China.
Instead of your company adjusting to the needs of a buying agent, I will comply with
your demands so everything you want comes to fruition.
➤Just tell us what exactly you want, we can give you a satisfied result or plan !
For more infomation, Pls feel free to contact me
Lee
Skype:+86 15919103357
WhatsApp:+86 15919103357
WeChat:15919103357
segunda-feira, 5 de junho de 2023
Insecure Features In PDFs
In 2019, we published attacks on PDF Signatures and PDF Encryption. During our research and studying the related work, we discovered a lot of blog posts, talks, and papers focusing on malicious PDFs causing some damage. However, there was no systematic analysis of all possible dangerous features supported by PDFs, but only isolated exploits and attack concepts.
We decided to fill this gap and systematize the possibilities to use legitimate PDF features and do bad stuff. We define four attack categories: Denial of Service, Information Disclosure, Data Manipulation, and Code Execution.
Our evaluation reveals 26 of 28 popular PDF processing applications are vulnerable to at least one attack. You can download all malicious PDFs here. You can also find more technical details in our NDSS'21 paper.
This is a joined work of Jens Müller, Dominik Noss, Christian Mainka, Vladislav Mladenov, and Jörg Schwenk.
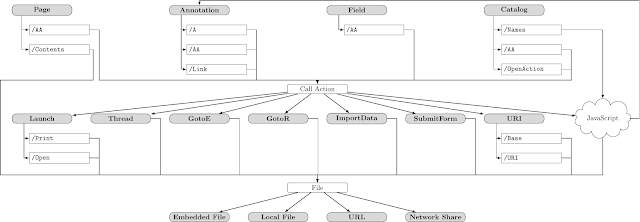
Dangerous Paths: Overview
We identified four PDF objects which allow calling arbitrary actions (Page, Annotation, Field, and Catalog). Most objects offer multiple alternatives for this purpose. For example, the Catalog object, defines the OpenAction or additional actions (AA) events. Each event can launch any sequence of PDF actions, for example, Launch, Thread, etc. JavaScript actions can be embedded within documents. It opens a new area for attacks, for example, new annotations can be created that can have actions which once again lead to accessing file handles.
Denial of Service
Infinite Loop
This variant induces an endless loop causing the program execution to get stuck. The PDF standard allows various elements of the document structure to reference to themselves, or to other elements of the same type.
- Action loop: PDF actions allow to specify a Next action to be performed, thereby resulting in "action cycles".
- ObjStm loop: Object streams may extend other object streams allows the crafting of a document with cycles.
- Outline loop: PDF documents may contain an outline. Its entries, however, can refer to themselves or each other.
- Calculations: PDF defines "Type 4" calculator functions, for example, to transform colors. Processing hard-to-solve mathematical formulas may lead to high demands of CPU.
- JavaScript: Finally, in case the PDF application processes scripts within documents, infinite loops can be induced.
Deflate Bomb
Information Disclosure
URL Invocation
PDF documents that silently "phone home" should be considered as privacy-invasive. They can be used, for example, to deanonymize reviewers, journalists, or activists behind a shared mailbox. The attack's goal is to open a backchannel to an attacker-controlled server once the PDF file is opened by the victim.
Form Data Leakage
Local File Leakage
The PDF standard defines various methods to embed external files into a document or otherwise access files on the host's file system, as documented below.
- External streams: Documents can contain stream objects (e.g., images) to be included from external files on disk.
- Reference XObjects: This feature allows a document to import content from another (external) PDF document.
- Open Prepress Interface: Before printing a document, local files can be defined as low-resolution placeholders.
- Forms Data Format (FDF): Interactive form data can be stored in, and auto-imported from, external FDF files.
- JavaScript functions: The Adobe JavaScript reference enables documents to read data from or import local files.
If a malicious document managed to firstly read files from the victim's disk and secondly, send them back to the attacker, such behavior would arguably be critical.
Credential Theft
Data Manipulation
Form Modification
File Write Access
Content Masking
The goal of this attack is to craft a document that renders differently, depending on the applied PDF interpreter. This can be used, for example, to show different content to different reviewers, to trick content filters (AI-based machines as well as human content moderators), plagiarism detection software, or search engines, which index a different text than the one shown to users when opening the document.
- Stream confusion: It is unclear how content streams are parsed if their Length value does not match the offset of the endstream marker, or if syntax errors are introduced.
- Object confusion: An object can overlay another object. The second object may not be processed if it has a duplicate object number, if it is not listed in the XRef table, or if other structural syntax errors are introduced.
- Document confusion: A PDF file can contain yet another document (e.g., as embedded file), multiple XRef tables, etc., which results in ambiguities on the structural level.
- PDF confusion: Objects before the PDF header or after an EOF marker may be processed by implementations, introducing ambiguities in the outer document structure.
Code Execution
Evaluation
Authors of this Post
Christian Mainka
Sources
[2] Aaron Spangler. WinNT/Win95 Automatic Authentication Vulnerability (IE Bug #4). https://insecure.org/sploits/winnt.automatic.authentication.html. Mar. 1997.
[3] Check Point Research. NTLM Credentials Theft via PDF Files. https://research.checkpoint.com/ntlm-credentials-theft-via-pdf-files/. 2018.
Related articles
- Easy Hack Tools
- Physical Pentest Tools
- Hacking Tools Github
- Hacking Tools Github
- Hacking Apps
- Pentest Tools Android
- Pentest Tools For Android
- Hacking Tools 2020
- Usb Pentest Tools
- Pentest Tools Find Subdomains
- Hacker Tools Linux
- Bluetooth Hacking Tools Kali
- Hack Tools Online
- Hacker Tool Kit
- Pentest Tools Android
- Hack Tools For Mac
- Hacker Tools Online
- Pentest Tools Alternative
- Pentest Tools Website
- Hacking Tools For Beginners
- Pentest Tools Online
- Hacker Search Tools
- Hacker Tools Windows
- Nsa Hack Tools
- New Hacker Tools
- Bluetooth Hacking Tools Kali
- Best Pentesting Tools 2018
- Pentest Tools Free
- Hacks And Tools
- Hacker Tools 2020
- Pentest Tools Nmap
- What Are Hacking Tools
- Hacker Security Tools
- Hacking Tools 2019
- Hacking Tools For Windows Free Download
- Hack Tools For Games
- World No 1 Hacker Software
- Hack Apps
- Hacker Tools Apk Download
- Hack App
- Hacking Tools For Windows
- Hack And Tools
- Hacking Tools For Games
- Pentest Tools Review
- Hacking App
- Pentest Tools Tcp Port Scanner
- Hacking Tools For Windows Free Download
- Pentest Automation Tools
- Hacker Tools Free
- Hacker Tools Apk
- Best Hacking Tools 2019
- Hack Tools Github
- Pentest Box Tools Download
- Hacking Tools For Pc
- Pentest Reporting Tools
- Pentest Recon Tools
- Best Pentesting Tools 2018
- Hack Tools For Windows
- Tools 4 Hack
- Hacker
- Pentest Tools Subdomain
- Blackhat Hacker Tools
- Hack Rom Tools
- Hack Tools
- Pentest Tools Open Source
- Hacking Tools For Beginners
- Hack App
- Hacker Techniques Tools And Incident Handling
- Pentest Tools Review
- Hacking Tools Online
- Hack Rom Tools
- Hacker Tools For Mac
- Pentest Tools Nmap
- Best Hacking Tools 2020
- Hacking Tools For Beginners
- Physical Pentest Tools
- Pentest Recon Tools
- Hacking Tools Kit
- Pentest Tools Kali Linux
- Hacker Tools 2020
- Hacking Tools For Kali Linux
- Hack Tools
- Pentest Tools For Android
- Hack App
- What Is Hacking Tools
- Pentest Tools Alternative
- Hacking Tools For Mac
- Pentest Tools For Windows
- Hack And Tools
- Hacking Tools 2019
- Hack Tool Apk
- Pentest Tools Nmap
- Kik Hack Tools
- Hack Tools For Mac
- Hacker
- Kik Hack Tools
- Hacker Tools Apk Download
- Hacking Tools Software
- How To Hack
- Hacking Tools Kit
- Hacker Tools 2020
- Pentest Tools Kali Linux
- Best Pentesting Tools 2018
- Hacker Tools List
- Pentest Tools Download
- Hacking Tools Free Download
- Game Hacking
- Pentest Box Tools Download
- Black Hat Hacker Tools
- Hacking Tools For Games
- Hacking Tools Online
- Hack Tool Apk No Root
- Hacker Tools
- Hacker Hardware Tools
- Hack Tools Mac
- Hack Tools For Games
- Pentest Tools Bluekeep
- New Hacker Tools
- Hack Apps
- Hacker Tools Linux
An Overview Of Exploit Packs (Update 25) May 2015
Added CVE-2015-0359 and updates for CVE-2015-0336
Update February 19, 2015
Added Hanjuan Exploit kit and CVE-2015-3013 for Angler
 |
| http://www.kahusecurity.com |
Added CVE-2015-3010, CVE-2015-3011 for Agler and a few reference articles.
If you notice any errors, or some CVE that need to be removed (were retired by the pack authors), please let me know. Thank you very much!
Update December 12, 2014
This is version 20 of the exploit pack table - see the added exploit packs and vulnerabilities listed below.
| Exploit Pack Table Update 20 |
|---|
| Click to view or download from Google Apps |
I want to give special thanks to Kafeine L0NGC47, Fibon and Curt Shaffer for their help and update they made. Note the new Yara rules sheet / tab for yara rules for exploit kit.
I also want to thank Kahu security, Kafeine, Malforsec and all security companies listed in References for their research.
If you wish to be a contributor (be able to update/change the exploits or add yara rules), please contact me :)
If you have additions or corrections, please email, leave post comments, or tweet (@snowfl0w) < thank you!
The Wild Wild West image was created by Kahu Security - It shows current and retired (retiring) kits.
| Gong Da / GonDad | Redkit 2.2 | x2o (Redkit Light) | Fiesta (=Neosploit) | Cool Styxy | DotkaChef | |
|---|---|---|---|---|---|---|
| CVE-2011-3544 | CVE-2013-2551 | CVE-2013-2465 | CVE-2010-0188 | CVE-2010-0188 | CVE-2012-5692 | |
| CVE-2012-0507 | CVE-2013-2471 | CVE-2013-0074/3896 | CVE-2011-3402 | CVE-2013-1493 | ||
| CVE-2012-1723 | CVE-2013-1493 | CVE-2013-0431 |
| CVE-2013-2423 | ||
| CVE-2012-1889 | CVE-2013-2460 | CVE-2013-0634 | CVE-2013-1493 | |||
| CVE-2012-4681 | CVE-2013-2551 | CVE-2013-2423 | ||||
| CVE-2012-5076 | ||||||
| CVE-2013-0422 | ||||||
| CVE-2013-0634 | ||||||
| CVE-2013-2465 |
| Angler | FlashPack = SafePack | White Lotus | Magnitude (Popads) | Nuclear 3.x | Sweet Orange |
|---|---|---|---|---|---|
| CVE-2013-0074/3896 | CVE-2013-0074/3896 | CVE-2011-3544 | CVE-2011-3402 | CVE-2010-0188 | CVE-2013-2423 |
| CVE-2013-0634 | CVE-2013-2551 | CVE-2013-2465 | CVE-2012-0507 | CVE-2012-1723 | CVE-2013-2471 |
| CVE-2013-2551 | CVE-2013-2551 | CVE-2013-0634 | CVE-2013-0422 | CVE-2013-2551 | |
| CVE-2013-5329 | CVE-2013-2460 | CVE-2013-2423 | |||
| CVE-2013-2471 ?? | CVE-2013-2471 | CVE-2013-2460 | |||
| CVE-2013-2551 | CVE-2013-2551 |
| CK | HiMan | Neutrino | Blackhole (last) | Grandsoft | Private EK |
|---|---|---|---|---|---|
| CVE-2011-3544 | CVE-2010-0188 | CVE-2013-0431 | CVE-2013-0422 | CVE-2010-0188 | CVE-2006-0003 |
| CVE-2012-1889 | CVE-2011-3544 | CVE-2013-2460 | CVE-2013-2460 | CVE-2011-3544 | CVE-2010-0188 |
| CVE-2012-4681 | CVE-2013-0634 | CVE-2013-2463* | CVE-2013-2471 | CVE-2013-0422 | CVE-2011-3544 |
| CVE-2012-4792* | CVE-2013-2465 | CVE-2013-2465* | and + all or some | CVE-2013-2423 | CVE-2013-1347 |
| CVE-2013-0422 | CVE-2013-2551 | CVE-2013-2551 | exploits | CVE-2013-2463 | CVE-2013-1493 |
| CVE-2013-0634 | * switch 2463*<>2465* | from the previous | CVE-2013-2423 | ||
| CVE-2013-3897 | Possibly + exploits | version | CVE-2013-2460 | ||
| * removed | from the previous | ||||
| version |
| Sakura 1.x | LightsOut | Glazunov | Rawin | Flimkit | Cool EK (Kore-sh) | Kore (formely Sibhost) |
|---|---|---|---|---|---|---|
| cve-2013-2471 | CVE-2012-1723 | CVE-2013-2463 | CVE-2012-0507 | CVE-2012-1723 | CVE-2013-2460 | CVE-2013-2423 |
| CVE-2013-2460 | CVE-2013-1347 | cve-2013-2471 | CVE-2013-1493 | CVE-2013-2423 | CVE-2013-2463 | CVE-2013-2460 |
| and + all or some | CVE-2013-1690 | CVE-2013-2423 | CVE-2013-2471 | CVE-2013-2463 | ||
| exploits | CVE-2013-2465 | CVE-2013-2471 | ||||
| from the previous | ||||||
| version |
| Styx 4.0 | Cool | Topic EK | Nice EK |
|---|---|---|---|
| CVE-2010-0188 | CVE-2012-0755 | CVE-2013-2423 | CVE-2012-1723 |
| CVE-2011-3402 | CVE-2012-1876 | ||
| CVE-2012-1723 | CVE-2013-0634 | ||
| CVE-2013-0422 | CVE-2013-2465 | ||
| CVE-2013-1493 | cve-2013-2471 | ||
| CVE-2013-2423 | and + all or some | ||
| CVE-2013-2460 | exploits | ||
| CVE-2013-2463 | from the previous | ||
| CVE-2013-2472 | version | ||
| CVE-2013-2551 | |||
| Social Eng |
=================================================================
The Explot Pack Table has been updated and you can view it here.
Exploit Pack Table Update 19.1 - View or Download from Google Apps
If you keep track of exploit packs and can/wish to contribute and be able to make changes, please contact me (see email in my profile)
I want to thank L0NGC47, Fibon, and Kafeine, Francois Paget, Eric Romang, and other researchers who sent information for their help.
Update April 28, 2013 - added CVE-2013-2423 (Released April 17, 2013) to several packs.
Now the following packs serve the latest Java exploit (update your Java!)
- Styx
- Sweet Orange
- Neutrino
- Sakura
- Whitehole
- Cool
- Safe Pack
- Crime Boss
- CritX
Other changes
Updated:
- Whitehole
- Redkit
- Nuclear
- Sakura
- Cool Pack
- Blackhole
- Gong Da
- KaiXin
- Sibhost
- Popads
- Alpha Pack
- Safe Pack
- Serenity
- SPL Pack
There are 5 tabs in the bottom of the sheet
- 2011-2013
- References
- 2011 and older
- List of exploit kits
- V. 16 with older credits

March 2013
The Explot Pack Table, which has been just updated, has migrated to Google Apps - the link is below. The new format will allow easier viewing and access for those who volunteered their time to keep it up to date.
In particular, I want to thank
L0NGC47, Fibon, and Kafeine for their help.
There are 5 tabs in the bottom of the sheet
- 2011-2013
- References
- 2011 and older
- List of exploit kits
- V. 16 with older credits
- Neutrino - new
- Cool Pack - update
- Sweet Orange - update
- SofosFO aka Stamp EK - new
- Styx 2.0 - new
- Impact - new
- CritXPack - new
- Gong Da - update
- Redkit - update
- Whitehole - new
- Red Dot - new
 The long overdue Exploit pack table Update 17 is finally here. It got a colorful facelift and has newer packs (Dec. 2011-today) on a separate sheet for easier reading.
The long overdue Exploit pack table Update 17 is finally here. It got a colorful facelift and has newer packs (Dec. 2011-today) on a separate sheet for easier reading.Updates / new entries for the following 13 packs have been added (see exploit listing below)
- Redkit
- Neo Sploit
- Cool Pack
- Black hole 2.0
- Black hole 1.2.5
- Private no name
- Nuclear 2.2 (Update to 2.0 - actual v. # is unknown)
- Nuclear 2.1 (Update to 2.0 - actual v. # is unknown)
- CrimeBoss
- Grandsoft
- Sweet Orange 1.1 Update to 1.0 actual v. # is unknown)
- Sweet Orange 1.0
- Phoenix 3.1.15
- NucSoft
- Sakura 1.1 (Update to 1.0 actual v. # is unknown)
- AssocAID (unconfirmed)
08-'12 |
for Wild Wild West graphic
- CVE-2011-0559 - Flash memory corruption via F-Secure
- CVE-2012-0507 - Java Atomic via Krebs on Security
- CVE-2011-3544 - Java Rhino via Krebs on Security
- CVE-2012-0507 - Java Atomic- after 1.8.91was released
- CVE-2011-3544 - Java Rhino
- CVE-2011-3521 - Java Upd.27 see Timo Hirvonen, Contagio, Kahu Security and Michael 'mihi' Schierl
- CVE-2011-2462 - Adobe PDF U3D
Also includes
"Flash pack" (presumably the same as before)
"Quicktime" - CVE-2010-1818 ?
- CVE-2012-0507 - Java Atomic
- CVE-2012-0507 - Java Atomic
- CVE-2011-3544 - Java Rhino + Java TC (in one file)

- CVE-2011-3544 Oracle Java Rhino
- CVE-2010-0840 JRE Trusted Method Chaining
- CVE-2010-0188 Acrobat Reader – LibTIFF
- CVE-2006-0003 MDAC
- CVE-2011-3544 - Java Rhino (It was in Exploitpack table v15, listing it to show all packs with this exploit)
- CVE-2012-0003 - WMP MIDI
- CVE-2011-1255 - IE Time Element Memory Corruption
- CVE-2011-2140 - Flash 10.3.183.x
- CVE-2011-2110 - Flash 10.3.181.x
- CVE-2010-0806 - IEPeers
- CVE-2011-2140 - Flash 10.3.183.x
- CVE-2012-0003 - WMP MIDI
- CVE-2011-3544 - Java Rhino
- CVE-2010-0886 - Java SMB
- CVE-2010-0840 - JRE Trusted Method Chaining
- CVE-2008-2463 - Snapshot
- CVE-2010-0806 - IEPeers
- CVE-2007-5659/2008-0655 - Collab.collectEmailInfo
- CVE-2008-2992 - util.printf
- CVE-2009-0927 - getIco
- CVE-2009-4324 - newPlayer
Additions - with many thanks to Kahu Security
Hierarchy Exploit Pack
=================
CVE-2006-0003
CVE-2009-0927
CVE-2010-0094
CVE-2010-0188
CVE-2010-0806
CVE-2010-0840
CVE-2010-1297
CVE-2010-1885
CVE-2011-0611
JavaSignedApplet
Siberia Private
==========
CVE-2005-0055
CVE-2006-0003
CVE-2007-5659
CVE-2008-2463
CVE-2008-2992
CVE-2009-0075
CVE-2009-0927
CVE-2009-3867
CVE-2009-4324
CVE-2010-0806
Techno XPack
===========
CVE-2008-2992
CVE-2010-0188
CVE-2010-0842
CVE-2010-1297
CVE-2010-2884
CVE-2010-3552
CVE-2010-3654
JavaSignedApplet
"Yang Pack"
=========
CVE-2010-0806
CVE-2011-2110
CVE-2011-2140
CVE-2011-354
Credits for the excellent Wild Wild West (October 2011 edition) go to kahusecurity.com
With many thanks to XyliBox (Xylitol - Steven), Malware Intelligence blog, and xakepy.cc for the information:
If you find any errors or CVE information for packs not featured , please send it to my email (in my profile above, thank you very much) .
- Blackhole 1.2.1 (Java Rhino added, weaker Java exploits removed)
- Blackhole 1.2.1 (Java Skyline added)
- Sakura Exploit Pack 1.0 (new kid on the block, private pack)
- Phoenix 2.8. mini (condensed version of 2.7)
- Fragus Black (weak Spanish twist on the original, black colored admin panel, a few old exploits added)

The full table in xls format - Version 14 can be downloaded from here.
The exploit pack table in XLSX format
The exploit pack table in csv format
P.S. There are always corrections and additions thanks to your feedback after the document release, come back in a day or two to check in case v.15 is out.
Kahusecurity issued an updated version of their Wild Wild West graphic that will help you learn Who is Who in the world of exploit packs. You can view the full version of their post in the link above.
- Bleeding Life 3.0
- Merry Christmas Pack (many thanks to kahusecurity.com)+
- Best Pack (many thanks to kahusecurity.com)
- Sava Pack (many thanks to kahusecurity.com)
- LinuQ
- Eleonore 1.6.5
- Zero Pack
- Salo Pack (incomplete but it is also old)
- Best Pack
- Blackhole Exploit 1.0
- Blackhole Exploit 1.1
- Bleeding Life 2.0
- Bleeding Life 3.0
- Bomba
- CRIMEPACK 2.2.1
- CRIMEPACK 2.2.8
- CRIMEPACK 3.0
- CRIMEPACK 3.1.3
- Dloader
- EL Fiiesta
- Eleonore 1.3.2
- Eleonore 1.4.1
- Eleonore 1.4.4 Moded
- Eleonore 1.6.3a
- Eleonore 1.6.4
- Eleonore 1.6.5
- Fragus 1
- Icepack
- Impassioned Framework 1.0
- Incognito
- iPack
- JustExploit
- Katrin
- Merry Christmas Pack
- Liberty 1.0.7
- Liberty 2.1.0*
- LinuQ pack
- Lupit
- Mpack
- Mushroom/unknown
- Open Source Exploit (Metapack)
- Papka
- Phoenix 2.0
- Phoenix 2.1
- Phoenix 2.2
- Phoenix 2.3
- Phoenix 2.4
- Phoenix 2.5
- Phoenix 2.7
- Robopak
- Salo pack
- Sava Pack
- SEO Sploit pack
- Siberia
- T-Iframer
- Unique Pack Sploit 2.1
- Webattack
- Yes Exploit 3.0RC
- Zero Pack
- Zombie Infection kit
- Zopack
----------------------------------------------
Bleeding Life 3.0
New Version Ad is here

Merry Christmas Pack read analysis atkahusecurity.com | Best Pack kahusecurity.comread analysis at | Sava Pack read analysis at kahusecurity.com |
Eleonore 1.6.5 [+] CVE-2011-0611 [+] CVE-2011-0559 [+] CVE-2010-4452 [-] CVE-2010-0886 | Salo Pack Old (2009), added just for the collection  | Zero Pack 62 exploits from various packs (mostly Open Source pack)  |
LinuQ pack Designed to compromise linux servers using vulnerable PHPMyAdmin. Comes with DDoS bot but any kind of code can be loaded for Linux botnet creation.LinuQ pack is PhpMyAdmin exploit pack with 4 PMA exploits based on a previous Russian version of the Romanian PMA scanner ZmEu. it is not considered to be original, unique, new, or anything special. All exploits are public and known well. It is designed to be installed on an IRC server (like UnrealIRCD). IP ranges already listed in bios.txt can be scanned, vulnerable IPs and specific PMA vulnerabilities will be listed in vuln.txt, then the corresponding exploits can be launched against the vulnerable server. It is more like a bot using PMA vulnerabilities than exploit pack. It is using CVE-2009-1148 (unconfirmed) CVE-2009-1149 (unconfirmed) CVE-2009-1150 (unconfirmed) CVE-2009-1151 (confirmed) | ||
====================================================================
See the list of packs covered in the list below
The full table in xls format - Version 12 can be downloaded from here.
Version 11 May 26, 2011 Changes:
- Phoenix2.7
- "Dloader" (well, dloader is a loader but the pack is some unnamed pack http://damagelab.org/lofiversion/index.php?t=20852)
- nuclear pack
- Katrin
- Robopak
- Blackhole exploit kit 1.1.0
- Mushroom/unknown
- Open Source Exploit kit
====================================================================
10. May 8, 2011 Version 10 Exploit Pack Table_V10May11
First, I want to thank everyone who sent and posted comments for updates and corrections.
*** The Wild Wild West picture is from a great post about evolution of exploit packs by Kahu Security Wild Wild West Update
As usual, send your corrections and update lists.
Go1Pack (not included) as reported as being a fake pack, here is a gui. Here is a threatpost article referencing it as it was used for an attack
- Eleonore 1.6.4
- Eleonore 1.6.3a
- Incognito
- Blackhole
Also, here is another article claiming it is not a fake http://community.websense.com/blogs/securitylabs/archive/2011/04/19/Mass-Injections-Leading-to-g01pack-Exploit-Kit.aspx
Go1 Pack CVE are reportedly
CVE-2006-0003
CVE-2009-0927
CVE-2010-1423
CVE-2010-1885
Does anyone have this pack or see it offered for sale?
Exploit kits I am planning to analyze and add (and/or find CVE listing for) are:
- Open Source Exploit Kit
- SALO
- K0de
Also, here is a great presentation by Ratsoul (Donato Ferrante) about Java Exploits (http://www.inreverse.net/?p=1687)
--------------------------------------------------------
9. April 5, 2011 Version 9 ExploitPackTable_V9Apr11
It actually needs another update but I am posting it now and will issue version 10 as soon as I can.
Changes:
Phoenix 2.5
IFramer
Tornado
Bleeding life
Many thanks to Gunther for his contributions.
If you wish to add some, please send your info together with the reference links. Also please feel free to send corrections if you notice any mistakes
- Eleonore 1.4.4 Moded added (thanks to malwareint.blogspot.com)
- Correction on CVE-2010-0746 in Phoenix 2.2 and 2.3. It is a mistake and the correct CVE is CVE-2010-0886 (thanks to ♫etonshell for noticing)
- SEO Sploit pack added (thanks to whsbehind.blogspot.com, evilcodecave.blogspot.com and blog.ahnlab.com)

Related news
- Pentest Recon Tools
- Hack Tools For Pc
- World No 1 Hacker Software
- Hacking Tools 2019
- Hack Tools 2019
- Nsa Hack Tools
- Black Hat Hacker Tools
- Nsa Hack Tools
- Hacker Tools Apk
- Pentest Tools Website Vulnerability
- What Are Hacking Tools
- Hack Rom Tools
- Hacking Tools For Mac
- Pentest Tools Find Subdomains
- Tools Used For Hacking
- Hacker Tools Software
- Pentest Tools Android
- Hacker Tools 2020
- Hacking Tools For Windows
- Hacker Tools For Pc
- Nsa Hack Tools Download
- Pentest Tools For Mac
- Hack Tools Mac
- Pentest Tools Windows
- Hacker Tools Online
- Hacker Tools Github
- Pentest Tools Review
- Hacker Security Tools
- Hacker Tools
- Hacker Security Tools
- Pentest Tools Linux
- Hacker Tools Apk Download
- Pentest Tools Alternative
- Hacker Tool Kit
- Pentest Tools Port Scanner
- Hacking Tools Software
- Usb Pentest Tools
- Hacker Search Tools
- Hacker Tools Hardware
- Hacking Tools Software
- Hack Tools Download
- Hack Tools
- Ethical Hacker Tools
- Growth Hacker Tools
- Pentest Recon Tools
- Hack Tool Apk
- Pentest Tools Nmap
- How To Install Pentest Tools In Ubuntu
- Hacking Tools And Software
- Hack Tools For Pc
- Hak5 Tools
- Hack Tools Mac
- Hack Tools For Ubuntu
- Hacker Tools Software
- Pentest Tools Framework
- Game Hacking
- Hack Tools Online
- Hack Tools For Windows
- Hackers Toolbox
- Pentest Box Tools Download
- Hack Tools Online
- Hack App
- Pentest Tools Windows
- Hacker Tools Hardware
- Pentest Tools Online
- Hack Tool Apk
- How To Make Hacking Tools
- Hacker Tools Online
- Hacking Tools Windows
- Pentest Tools Subdomain
- Game Hacking
- Pentest Tools For Ubuntu
- Hacking Tools 2019
- Beginner Hacker Tools
- Bluetooth Hacking Tools Kali
- Hacker Tools Github
- Usb Pentest Tools
- Hack Tools For Games
- Hacker Tools Windows
- Hacker Tools Apk
- Hacking Tools For Windows
- Hacking Tools Usb
- Hacks And Tools
- Hacker Techniques Tools And Incident Handling
- Hack Tools Download
- Hacker Tools Linux
- Hacking Tools Download
- Pentest Tools Subdomain
- Pentest Tools Url Fuzzer
- Hacking Tools Pc
- Hack Tools Download
- Pentest Tools
- Hack Tools Online
- Pentest Tools Nmap
- Hacking Tools Software
- Github Hacking Tools
- Ethical Hacker Tools
- Hacking App
- Hacker Tools List
- Hacker Tools For Pc
- Hacker Tools For Pc
- Hacking Tools
- Ethical Hacker Tools
- Pentest Tools Apk
- Free Pentest Tools For Windows
- Hacker Tools Apk
- World No 1 Hacker Software
- Hacker Tools Hardware
- Nsa Hack Tools
- Hacking Tools Github
- Hacker Tools 2019
- Best Hacking Tools 2020
- Bluetooth Hacking Tools Kali
- Pentest Tools For Mac
- Beginner Hacker Tools
- Hack Tools Download
- Hack Tools Github
- Hack Tools For Mac
- Pentest Tools Review
- Hack Tools For Ubuntu
- Pentest Tools Review
- Pentest Tools Bluekeep
- Pentest Tools Apk
- Hacking Tools For Games
- Pentest Tools Review
- Hacking Tools Kit
- Hacker Tools For Windows
- Underground Hacker Sites
- Game Hacking
- Underground Hacker Sites
- Pentest Tools Apk
- Pentest Tools Website Vulnerability
- Pentest Tools Free
- Hacking Tools Mac
- Hacking Tools Download
- Hacking Tools For Games
- Hacking Tools Github
- Hack Tools Pc
- Best Hacking Tools 2020
- Hacking App
- Pentest Tools Framework
- Pentest Tools Kali Linux
- Hack Tools For Games
- Hacking Tools For Windows
- Hacker Tools Apk Download
- Hacking Tools For Windows Free Download
- Hacking Tools For Beginners
- Hack Tools Online
- Hacker Tools Apk
- Tools Used For Hacking
- Pentest Automation Tools
- Hacking Tools Pc
- Pentest Tools Online
- Pentest Tools Alternative
- Hacking Tools Github
- Hack Tool Apk No Root
- Blackhat Hacker Tools
- Hacker Search Tools
- Pentest Tools
- Computer Hacker
- Pentest Box Tools Download
- Pentest Tools Port Scanner